7001 Corporate Dr, Suite 120
Houston, TX 77036
IT Disaster Recovery Plan
Revision History
| revision | date | name | description |
| Original 1.0 | |||
Table of Contents
1.2 Plan Documentation Storage. 12
2.1 Alert, escalation and plan invocation.. 13
2.1.1 Plan Triggering Events. 13
2.1.3 Activation of Emergency Response Team.. 13
2.2 Disaster Recovery Team.. 14
2.3 Emergency Alert, Escalation and DRP Activation.. 14
2.3.2 DR Procedures for Management 15
2.3.3 Contact with Employees. 15
2.3.5 Personnel and Family Notification. 15
3.4 Rules for Dealing with Media. 16
5 Financial and Legal Issues. 17
5.2 Financial Requirements. 17
Appendix A – Technology Disaster Recovery Plan Templates. 18
Disaster Recovery Plan for Server 1. 18
Disaster Recovery Plan for Server 2. 20
Disaster Recovery Plan for Server 3. 22
Disaster Recovery Plan for Local Area Network (LAN) 23
Network Diagram as of 6/7/2012. 24
ASA Firewall Configs as of 6/7/2012. 25
Disaster Recovery Plan for Wide Area Network (WAN) 32
Disaster Recovery Plan for Voice Communications. 34
Appendix B – Suggested Forms. 36
Management of DR Activities Form.. 36
Disaster Recovery Event Recording Form.. 36
Disaster Recovery Activity Report Form.. 37
Mobilizing the Disaster Recovery Team Form.. 38
Mobilizing the Business Recovery Team Form.. 38
Monitoring Business Recovery Task Progress Form.. 39
Preparing the Business Recovery Report Form.. 39
Returning Recovered Business Operations to Business Unit Leadership. 40
Business Process/Function Recovery Completion Form.. 40
Information Technology Statement of Intent
This document delineates our policies and procedures for technology disaster recovery, as well as our process-level plans for recovering critical technology platforms and the telecommunications infrastructure. This document summarizes our recommended procedures. In the event of an actual emergency situation, modifications to this document may be made to ensure physical safety of our people, our systems, and our data.
Our mission is to ensure information system uptime, data integrity and availability, and business continuity.
Policy Statement
Corporate management has approved the following policy statement:
· The clinic shall develop a comprehensive IT disaster recovery plan.
· A formal risk assessment shall be undertaken to determine the requirements for the disaster recovery plan.
· The disaster recovery plan should cover all essential and critical infrastructure elements, systems and networks, in accordance with key business activities.
· The disaster recovery plan should be periodically tested in a simulated environment to ensure that it can be implemented in emergency situations and that the management and staff understand how it is to be executed.
· All staff must be made aware of the disaster recovery plan and their own respective roles.
· The disaster recovery plan is to be kept up to date to take into account changing circumstances.
Objectives
The principal objective of the disaster recovery program is to develop, test and document a well-structured and easily understood plan which will help the company recover as quickly and effectively as possible from an unforeseen disaster or emergency which interrupts information systems and business operations. Additional objectives include the following:
• The need to ensure that all employees fully understand their duties in implementing such a plan
• The need to ensure that operational policies are adhered to within all planned activities
• The need to ensure that proposed contingency arrangements are cost-effective
• Disaster recovery capabilities as applicable to key customers, vendors and others
Key Personnel Contact Info
| Name, Title | Contact Option | Contact Number |
| Andrea Caracostis | Work | (713) 773-0803 Ext 110 |
| | Mobile | 713-254-2235 |
| | Email Address | |
| | ||
| SukJun Cheng | Work | (713) 773-0803 Ext 121 |
| Mobile | 832-877-3738 | |
| | Email Address | |
| | ||
| Richard R Andrews | Work | (713) 773-0803 Ext 106 |
| | Mobile | 281-408-6427 |
| | Email Address | |
| | ||
| Shane Chen | Work | (713) 773-0803 Ext 105 |
| | Mobile | 713-398-4849 |
| | Email Address | |
| Victor Rodriguez | Work | (713) 773-0803 Ext 127 |
| | Mobile | 832-283-0651 |
| | Email Address | |
| | ||
| Norma McCoy | Work | (713) 773-0803 Ext 115 |
| | Mobile | 832-896-8971 |
| | Email Address | |
| |
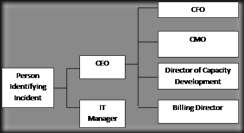
Notification Calling Tree
 |
External Contacts
| Name, Title | Contact Option | Contact Number |
| Landlord / Property Manager - | 7001 Corporate Investment Partner | |
| Account Number | Phone | 281-222-1678 |
| 7001 Corporate Dr, Suite 120 Houston, TX 77036 | ||
| | ||
| Power Company - | Reliant Energy | |
| Account Number | Phone | 713-207-7777 |
| | Address | P.O. Box 3765, Houston, TX 77253-3765 |
| | Web Site | http://www.reliant.com/Welcome.do;jsessionid=A3562B9178B06815579E9D7CA5F0ADE5 |
| | | |
| | ||
| T1 Carrier - | TACHC | |
| Account Number | Work | (512) 329-5959 |
| | Fax | (512) 329-9189 |
| | Address | 5900 Southwest Parkway, Building 3 Austin, TX 78735 |
| | Email Address | Lee Davila ldavila@tachc.org |
| | Web Site | |
| | ||
| T1 Carrier – Medicaid - | AT&T | |
| Account Number | Phone | 1-888-944-0447 |
| | Support | 1-800-248-3632 |
| | eContact | |
| | Web Site | |
| | ||
| PBX Carrier - | Logix | |
| Account Number | Phone | Main: (713) 862-2000 |
| | Phone | 1-800-444-0258 |
| | Fax | (713) 333-8731 |
| | Address | 2950 N. Loop W., 8th Floor Houston, TX 77092 |
| | Sales Email Address | |
| | Voice Help Desk | 1-877-722-5283 |
| | Web Site | |
| | ||
| Hardware Supplier - | Directron | |
| Account Number | Work | 713-773-9898 |
| | Address | 10402 Harwin Drive Houston, Texas 77036, USA |
| | Tech Phone Number | 713-773-3636 x1700 |
| | Sales Email Address | |
| | Tech Email Address | |
| | ||
| Server Supplier - | Dell | |
| Account Number. | Phone | 1-800-274-1550 |
| | Web Site | http://content.dell.com/us/en/healthcare/healthcare-solutions.aspx?~ck=mn |
| | eContact | |
| | Tech Support | 1-800-822-8965 |
| | ||
| Workstation Supplier - | HP | |
| Account Number | Support | 866-625-0242 Option #1 |
| | Sales | 866-625-0242 Option #2 |
| | Customer Service | 866-625-0242 Option #3 |
| | Web Site | |
| | ||
| Office Supplies - | Staples | |
| Account Number | Phone | 713-777-0614 |
| | Fax | 713-777-0683 |
| | Address | 8225 S. Gessner Rd Suite A, Houston, TX 77036 |
| | Web Site | |
| | ||
| Insurance – | Frost Insurance | |
| Account Number | Work | 713-388-1250 |
| | Fax | 713-388-1238 |
| | Address | 3707 Richmond Ave Houston, TX 77046 |
| | Web Site | https://www.frostbank.com/Pages/Business-Property-Liability-Insurance.aspx |
| | ||
| Electronic Health Record - | Sevocity Electronic Health Records | |
| Account Number | Phone | 877-777-2298 |
| Address | 9830 Colonnade Blvd., Suite 377 San Antonio, TX 78230-2202 | |
| Web Site | ||
| Email address | ||
| Trouble ticketing | ||
| Practice Management - | Medical Systems, Inc. | |
| Account Number | Phone | (978) 531-6000 |
| Address | Peabody Education and Business Center, 83 Pine Street | |
| Web Site | ||
| Email Address | ||
| Sales Contact | Helen Marie Simms | |
| Trouble Ticketing | ||
| User Name/Password | ||
| HCN (Platinum) - | Health Choice Network | |
| Account Number | Phone | (305) 599-1015 ext. 18019 |
| Address | 9000 N.W. 15 Street, Miami, FL 33172 | |
| Mailing Address | 9064 N.W. 13 Terrace, Miami, FL 33172 | |
| Web Site | ||
| Email Address | ||
| Sales Contact | Iliana Farinas | |
| Trouble Ticketing | ||
| User Name/Password | hcn\[UserName] login password |
External Contacts Calling Tree
1 Plan Overview
1.1 Plan Updating
It is necessary for the DRP updating process to be properly structured and controlled. Whenever changes are made to the plan they are to be fully tested and appropriate amendments should be made to the training materials. This will involve the use of formalized change control procedures under the control of the IT Director.
1.2 Plan Documentation Storage
Copies of this Plan, CD, and hard copies will be stored in secure locations to be defined by the company. Each member of senior management will be issued a CD and hard copy of this plan to be filed at home. Each member of the Disaster Recovery Team and the Business Recovery Team will be issued a CD and hard copy of this plan. A master protected copy will be stored on specific resources established for this purpose.
1.3 Backup Strategy
Key business processes and the agreed backup strategy for each are listed below. The strategy chosen is for full backups to be maintained at the TACHC offices in Austin, TX. This strategy entails the maintenance of hosted applications which will enable online access.
| KEY BUSINESS PROCESS | BACKUP STRATEGY |
| IT Operations | Off-site data storage facility |
| | Off-site data storage facility |
| Disaster Recovery | Off-site data storage facility |
| Finance | Off-site data storage facility |
| Human Resources | Off-site data storage facility |
| Web Site | Off-site data storage facility |
1.4 Risk Management
There are many potential disruptive threats which can occur at any time and affect the normal business process. We have considered a wide range of potential threats and the results of our deliberations are included in this section. Each potential environmental disaster or emergency situation has been examined. The focus here is on the level of business disruption which could arise from each type of disaster.
Potential disasters have been assessed as follows:
| Potential Disaster | Probability Rating | Impact Rating | Brief Description Of Potential Consequences & Remedial Actions |
| Flood | 3 | 4 | All critical equipment is located on 1st Floor |
| Fire | 3 | 4 | FM200 suppression system installed in main computer centers. Fire and smoke detectors on all floors. |
| Tornado | 5 | ||
| Electrical storms | 5 | ||
| Act of terrorism | 5 | ||
| Act of sabotage | 5 | ||
| Electrical power failure | 3 | 4 | Redundant UPS array together with auto standby generator that is tested weekly & remotely monitored 24/7. UPSs also remotely monitored. |
| Loss of communications network services | 4 | 4 | Two diversely routed T1 trunks into building. WAN redundancy, voice network resilience |
Probability: 1=Very High, 5=Very Low Impact: 1=Total destruction, 5=Minor annoyance
2 Emergency Response
2.1 Alert, escalation and plan invocation
2.1.1 Plan Triggering Events
Key trigger issues at the clinic that would lead to activation of the DRP are:
• Total loss of all communications
• Total loss of power
• Flooding of the premises
• Fire on the premises
• Loss of the building
2.1.2 Assembly Points
Where the premises need to be evacuated, the DRP invocation plan identifies two evacuation assembly points:
• Primary – Far end of main parking lot;
• Alternate – Parking lot of company across the street
2.1.3 Activation of Emergency Response Team
When an incident occurs the Emergency Response Team (ERT) must be activated. The ERT will then decide the extent to which the DRP must be invoked. All employees must be issued a Quick Reference card containing ERT contact details to be used in the event of a disaster. Responsibilities of the ERT are to:
• Respond immediately to a potential disaster and call emergency services;
• Assess the extent of the disaster and its impact on the business, data center, etc.;
• Decide which elements of the DR Plan should be activated;
• Establish and manage disaster recovery team to maintain vital services and return to normal operation;
• Ensure employees are notified and allocate responsibilities and activities as required.
2.2 Disaster Recovery Team
The team will be contacted and assembled by the ERT. The team's responsibilities include:
• Establish facilities for an emergency level of service within 2.0 business hours;
• Restore key services within 4.0 business hours of the incident;
• Recover to business as usual within 8.0 to 24.0 hours after the incident;
• Coordinate activities with disaster recovery team, first responders, etc.
• Report to the emergency response team.
2.3 Emergency Alert, Escalation and DRP Activation
This policy and procedure has been established to ensure that in the event of a disaster or crisis, personnel will have a clear understanding of who should be contacted. Procedures have been addressed to ensure that communications can be quickly established while activating disaster recovery.
The DR plan will rely principally on key members of management and staff who will provide the technical and management skills necessary to achieve a smooth technology and business recovery. Suppliers of critical goods and services will continue to support recovery of business operations as the company returns to normal operating mode.
2.3.1 Emergency Alert
The person discovering the incident calls a member of the Emergency Response Team in the order listed:
Emergency Response Team
• Andrea Caracostis
• Richard Andrews
• Shane Chen
If not available try:
• Suk Jun Cheng
• Victor Rodriguez
The Emergency Response Team (ERT) is responsible for activating the DRP for disasters identified in this plan, as well as in the event of any other occurrence that affects the company’s capability to perform normally.
One of the tasks during the early stages of the emergency is to notify the Disaster Recovery Team (DRT) that an emergency has occurred. The notification will request DRT members to assemble at the site of the problem and will involve sufficient information to have this request effectively communicated. The Business Recovery Team (BRT) will consist of senior representatives from the main business departments. The BRT Leader will be a senior member of the company's management team, and will be responsible for taking overall charge of the process and ensuring that the company returns to normal working operations as early as possible.
2.3.2 DR Procedures for Management
Members of the management team will keep a hard copy of the names and contact numbers of each employee in their departments. In addition, management team members will have a hard copy of the company’s disaster recovery and business continuity plans on file in their homes in the event that the clinic building is inaccessible, unusable, or destroyed.
2.3.3 Contact with Employees
Managers will serve as the focal points for their departments, while designated employees will call other employees to discuss the crisis/disaster and the company’s immediate plans. Employees who cannot reach staff on their call list are advised to call the staff member’s emergency contact to relay information on the disaster.
2.3.4 Backup Staff
If a manager or staff member designated to contact other staff members is unavailable or incapacitated, the designated backup staff member will perform notification duties.
2.3.5 Personnel and Family Notification
If the incident has resulted in a situation which would cause concern to an employee’s immediate family such as hospitalization of injured persons, it will be necessary to notify their immediate family members quickly.
3 Media
3.1 Media Contact
Assigned staff will coordinate with the media, working according to guidelines that have been previously approved and issued for dealing with post-disaster communications.
3.2 Media Strategies
1. Avoiding adverse publicity
2. Take advantage of opportunities for useful publicity
3. Have answers to the following basic questions:
· What happened?
· How did it happen?
· What are you going to do about it?
3.3 Media Team
• Andrea Caracostis _
• Richard Andrews _
• Shane Chen _
3.4 Rules for Dealing with Media
Only the media team is permitted direct contact with the media; anyone else contacted should refer callers or in-person media representatives to the media team.
4 Insurance
As part of the company’s disaster recovery and business continuity strategies a number of insurance policies have been put in place. These include errors and omissions, directors & officers liability, general liability, and business interruption insurance.
If insurance-related assistance is required following an emergency out of normal business hours, please contact:
| Policy Name | Coverage Type | Coverage Period | Amount Of Coverage | Person Responsible For Coverage | Next Renewal Date |
| Frost Insurance | Liability | | | | |
| | | | | | |
| | | | | | |
5 Financial and Legal Issues
5.1 Financial Assessment
The emergency response team shall prepare an initial assessment of the impact of the incident on the financial affairs of the company. The assessment should include:
· Loss of financial documents
· Loss of revenue
· Theft of check books, credit cards, etc.
· Loss of cash
5.2 Financial Requirements
The immediate financial needs of the company must be addressed. These can include:
· Cash flow position
· Temporary borrowing capability
· Upcoming payments for taxes, payroll taxes, Social Security, etc.
· Availability of company credit cards to pay for supplies and services required post-disaster
5.3 Legal Actions
The company legal department and ERT will jointly review the aftermath of the incident and decide whether there may be legal actions resulting from the event; in particular, the possibility of claims by or against the company for regulatory violations, etc.
6 DRP Exercising
Disaster recovery plan exercises are an essential part of the plan development process. In a DRP exercise no one passes or fails; everyone who participates learns from exercises – what needs to be improved, and how the improvements can be implemented. Plan exercising ensures that emergency teams are familiar with their assignments and, more importantly, are confident in their capabilities.
Successful DR plans launch into action smoothly and effectively when they are needed. This will only happen if everyone with a role to play in the plan has rehearsed the role one or more times. The plan should also be validated by simulating the circumstances within which it has to work and seeing what happens.
Appendix B – Suggested Forms
Damage Assessment Form
| Key Business Process Affected | Description Of Problem | Extent Of Damage |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
_____________
Management of DR Activities Form
• During the disaster recovery process all activities will be determined using a standard structure;
• Where practical, this plan will need to be updated on a regular basis throughout the disaster recovery period;
• All actions that occur during this phase will need to be recorded.
| Activity Name: |
| Reference Number: |
| Brief Description:
|
| Commencement Date/Time | Completion Date/Time | Resources Involved | In Charge |
__________________
Disaster Recovery Event Recording Form
• All key events that occur during the disaster recovery phase must be recorded.
• An event log shall be maintained by the disaster recovery team leader.
• This event log should be started at the commencement of the emergency and a copy of the log passed on to the business recovery team once the initial dangers have been controlled.
• The following event log should be completed by the disaster recovery team leader to record all key events during disaster recovery, until such time as responsibility is handed over to the business recovery team.
| Description of Disaster: |
| Commencement Date: |
| Date/Time DR Team Mobilized: |
| Activities Undertaken by DR Team | Date and Time | Outcome | Follow-On Action Required |
| Disaster Recovery Team's Work Completed: <Date> |
| Event Log Passed to Business Recovery Team: <Date> |
_________________
Disaster Recovery Activity Report Form
• On completion of the initial disaster recovery response the DRT leader should prepare a report on the activities undertaken.
• The report should contain information on the emergency, who was notified and when, action taken by members of the DRT together with outcomes arising from those actions.
• The report will also contain an assessment of the impact to normal business operations.
• The report should be given to business recovery team leader, with a copy to senior management, as appropriate.
• A disaster recovery report will be prepared by the DRT leader on completion of the initial disaster recovery response.
• In addition to the business recovery team leader, the report will be distributed to senior management
The report will include:
• A description of the emergency or incident
• Those people notified of the emergency (including dates)
• Action taken by members of the DRT
• Outcomes arising from actions taken
• An assessment of the impact to normal business operations
• Assessment of the effectiveness of the BCP and lessons learned
• Lessons learned
__________
Mobilizing the Disaster Recovery Team Form
• Following an emergency requiring recovery of technology infrastructure assets, the disaster recovery team should be notified of the situation and placed on standby.
• The format shown below can be used for recording the activation of the DR team once the work of the damage assessment and emergency response teams has been completed.
| Description of Emergency: |
| Date Occurred: |
| Date Work of Disaster Recovery Team Completed: |
| Name of Team Member | Contact Details | Contacted On (Time / Date) | By Whom | Response | Start Date Required |
| Relevant Comments (e.g., Specific Instructions Issued) |
___________
Mobilizing the Business Recovery Team Form
· Following an emergency requiring activation of the disaster recovery team, the business recovery team should be notified of the situation and placed on standby.
· The format shown below will be used for recording the activation of the business recovery team once the work of the disaster recovery team has been completed.
| Description of Emergency: |
| Date Occurred: |
| Date Work of Business Recovery Team Completed: |
| Name of Team Member | Contact Details | Contacted On (Time / Date) | By Whom | Response | Start Date Required |
| Relevant Comments (e.g., Specific Instructions Issued) |
____________
Monitoring Business Recovery Task Progress Form
• The progress of technology and business recovery tasks must be closely monitored during this period of time.
• Since difficulties experienced by one group could significantly affect other dependent tasks it is important to ensure that each task is adequately resourced and that the efforts required to restore normal business operations have not been underestimated.
Note: A priority sequence must be identified although, where possible, activities will be carried out simultaneously.
| Recovery Tasks (Order of Priority) | Person(s) Responsible | Completion Date | Milestones Identified | Other Relevant Information | |
| Estimated | Actual | ||||
| 1. | |||||
| 2. | |||||
| 3. | |||||
| 4. | |||||
| 5. | |||||
| 6. | |||||
| 7. | |||||
___________
Preparing the Business Recovery Report Form
· On completion of business recovery activities the BRT leader should prepare a report on the activities undertaken and completed.
· The report should contain information on the disruptive event, who was notified and when, action taken by members of the BRT together with outcomes arising from those actions.
· The report will also contain an assessment of the impact to normal business operations.
· The report should be distributed to senior management, as appropriate.
The contents of the report shall include:
· A description of the incident
· People notified of the emergency (including dates)
· Action taken by the business recovery team
· Outcomes arising from actions taken
· An assessment of the impact to normal business operations
· Problems identified
· Suggestions for enhancing the disaster recovery and/or business continuity plan
· Lessons learned
Communications Form
· It is very important during the disaster recovery and business recovery activities that all affected persons and organizations are kept properly informed.
· The information given to all parties must be accurate and timely.
· In particular, any estimate of the timing to return to normal working operations should be announced with care.
· It is also very important that only authorized personnel deal with media queries.
| Groups of Persons or Organizations Affected by Disruption | Persons Selected To Coordinate Communications to Affected Persons / Organizations | ||
| Name | Position | Contact Details | |
| Customers | |||
| Management & Staff | |||
| Suppliers | |||
| Media | |||
| Stakeholders | |||
| Others |
____________
Returning Recovered Business Operations to Business Unit Leadership
· Once normal business operations have been restored it will be necessary to return the responsibility for specific operations to the appropriate business unit leader.
· This process should be formalized in order to ensure that all parties understand the change in overall responsibility, and the transition to business-as-usual.
· It is likely that during the recovery process, overall responsibility may have been assigned to the business recovery process lead.
· It is assumed that business unit management will be fully involved throughout the recovery, but in order for the recovery process to be fully effective, overall responsibility during the recovery period should probably be with a business recovery process team.
____________
Business Process/Function Recovery Completion Form
The following transition form should be completed and signed by the business recovery team leader and the responsible business unit leader, for each process recovered.
A separate form should be used for each recovered business process.
| Name Of Business Process | |
| Completion Date of Work Provided by Business Recovery Team | |
| Date of Transition Back to Business Unit Management (If different than completion date) | |
| I confirm that the work of the business recovery team has been completed in accordance with the disaster recovery plan for the above process, and that normal business operations have been effectively restored. Business Recovery Team Leader Name: ________________________________________ Signature: ________________________________________________________________ Date: __________________________
(Any relevant comments by the BRT leader in connection with the return of this business process should be made here.)
| |
| I confirm that above business process is now acceptable for normal working conditions. Name: ___________________________________________________________________ Title: ____________________________________________________________________ Signature: ________________________________________________________________ Date: __________________________ |